Update #17 - Installing Root Kit Detection on Virtual Private Server
Date: May 30, 2025
Category: Security / System Monitoring
I am going to install rootkit detection on my VPS. This is good practice, although not many Linux servers are attacked in this way.
In this guide, I'll be installing and using chkrootkit and rkhunter.
Update and Upgrade:
sudo apt update && sudo apt upgrade -yInstall chkrootkit :
sudo apt install chkrootkit -yRun the scan:
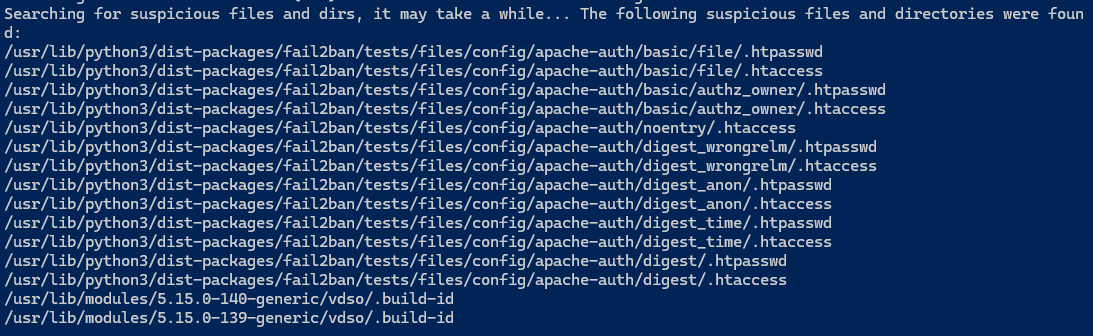
sudo chkrookitThere was nothing found in most cases, but since I use Fail2Ban , these files are from its own test files, which include .htpasswd and .htaccessexamples. These are not actually security threats and are normal and expected.chrootkitflags these because .htaccess and .htpasswd can sometimes hide malicious behavior - but in this context, they're safe.
The two .build-id are also normal and expected. They are part of the Linux Kernel's vdso(Virtually Dynamically-linked Shared Object), which helps with performance for certain syscalls.
So this is clean, chrootkit is doing its job of alerting me of potentially dangerous file types, not actual infections.
In this case, all flagged items are false positives.
Now I'm going to move on and install RKHunter:
1.) Install RKHunter
sudo apt update
sudo apt install rkhunter -y2.) Open RKHunter's Config File:
sudo nano /etc/rkhunter.confModify the following
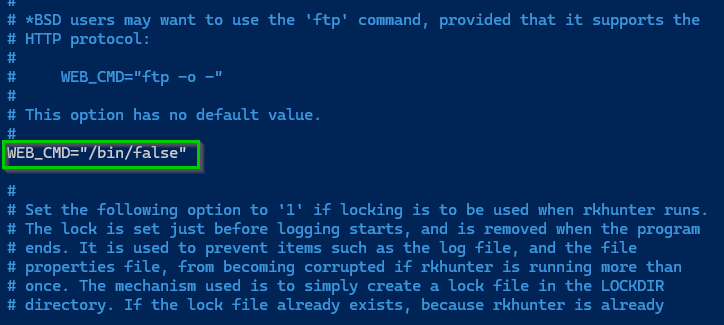
Comment this out: use Ctrl + W to search the file and then type WEB_CMD
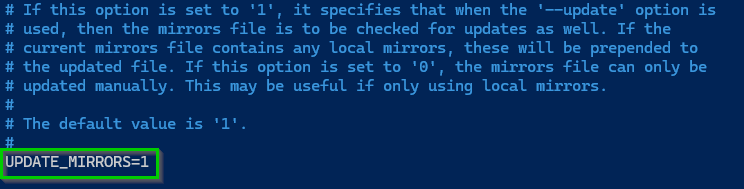
Use CTRL+W to search for UPDATE_MIRRORS and change it to 1
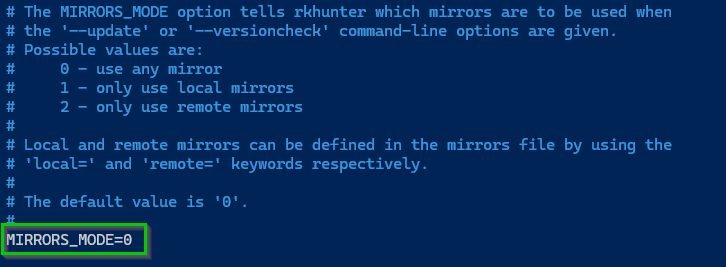
Do the same for MIRRORS_MODE and set that to 0
3.) Update RKHunter's Data Files
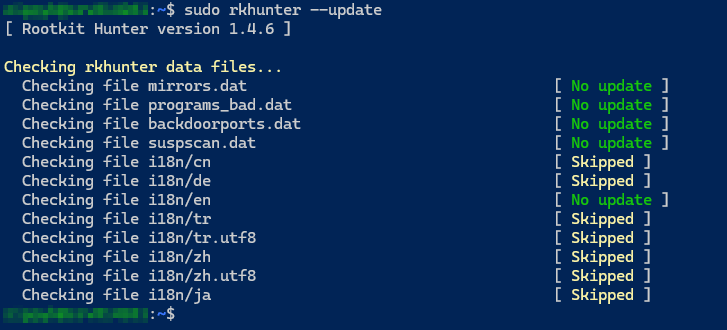
sudo rkhunter --updateThis pulls the latest rootkit definitions and mirror lists.
This is what you want it to look like, since it was freshly installed, nothing new was added:
Now lets run it:
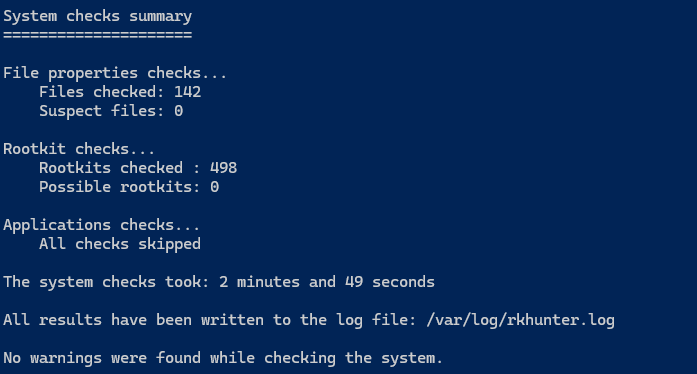
sudo rkhunter --checkIt will check for possible root kits and the output should look like this:
Now you will have to make key presses by hitting ENTER to continue, in order to automate this we can run:
sudo rkhunter --check --skor the full command:
sudo rkhunter --check --skip-keypressThis will be useful when saving it to a logfile or scheduling it as a cron job.
It runs the scan fully unattended.
You can save the output.
Allows for scripts or email alerts!

No Comments